In today’s modern business world, your biggest decision isn’t just if you’ll move your infrastructure to the cloud. It’s how you’ll do it safely. Amazon Web Services (AWS) is the top cloud platform globally. It hosts everything from basic websites to critical financial systems. While AWS gives you a strong foundation, protecting your assets there is a huge job. It directly affects your whole organization’s future.
Here’s the deal: Moving to the cloud makes you fast and lets you grow big. But it also brings new security worries. You simply can’t use the old security practices that worked in your building’s data center. The cloud moves extremely fast. This means security can’t be a single check mark anymore. It must become a continuous, automated process that always keeps up.
This article is your full roadmap. We designed it especially for technical leaders. You’ll get a clear plan for protecting your AWS cloud setups. We’ll explain the main ideas, the biggest problems, and the essential AWS security best practices you need to start today. When you finish this guide, you’ll know exactly how to secure AWS infrastructures and build truly strong systems. Our main point is this: AWS cloud security is a shared management task. It needs a mix of native AWS tools, automation, and clear policies to work right. Let’s dive in.
What is AWS cloud security?
Put simply, AWS cloud security is the full set of strategies, rules, practices, and technologies you use to protect your data, applications, and infrastructure running on the Amazon Web Services platform. It means combining its built-in security for AWS features with your organization’s own controls. This keeps your cloud assets private, intact, and available when you need them.
It’s much more than just using a firewall. AWS cloud security includes the whole digital and physical environment. This covers things like:
- Identity and Access Management (IAM): This controls who can access what resources.
- Data protection: This means encryption for data sitting in storage (at rest) and data moving across networks (in transit).
- Network security: This is about separating your virtual networks (VPC) to control where traffic flows.
- Threat detection and response: This involves monitoring for suspicious activity. Then, you take fast action to detect and stop threats.
- Compliance: This means following all mandatory rules, like HIPAA, PCI DSS, or GDPR.
AWS offers a huge number of built-in security solutions and tools. These help businesses meet tough operational rules and compliance needs. However, it’s critical to remember that security in the cloud isn’t just automatic. The platform gives you the alarm systems and the keys. But you have to lock the doors and set the alarm. Without proper planning and using AWS security best practices, even the best infrastructure can be easily exposed.
Traditional IT security vs. cloud security
Moving your data center from physical servers to the cloud is a core shift. It’s not just a hardware update. Because of this, you must change your whole approach to security.
So, what’s different? It all comes down to control and speed.
| Feature | Traditional On-Premise Security | Amazon Web Services Cloud Security |
| Infrastructure Control | You control 100% of the hardware, physical servers, and operating systems. | Control is virtual. AWS handles the physical layer – the actual building and hardware. |
| Scale and Scope | Fixed size; setting up new hardware takes weeks or months. | It grows big quickly; setting up new resources takes minutes or seconds. |
| Firewalls & Networking | Physical firewalls, routers, and switches. | Software-defined networks; virtual firewalls (Security Groups, NACLs). |
| Patching & Updates | Your team patches all operating systems and software. | Shared job: AWS patches the core infrastructure; you patch your guest systems and OS. |
| Security Mindset | Focus is on defending the edge of the network (the “castle-and-moat” idea). | Focus is on identity, configuration, and data encryption (the “zero-trust” idea). |
The key difference is automation. In the cloud, security is defined by software. Instead of setting up a physical firewall by hand, you write code (Infrastructure as Code, or IaC). This code defines a virtual firewall. This new way lets you manage security with amazing speed and consistency.
Think about this: In the old way, a security patch meant lengthy coordination and system downtime. In cloud security in AWS, an automated update goes out across hundreds of virtual systems instantly. This speed is great. But it also means a small mistake in your automation can cause a huge security flaw very quickly. The main ideas of good management stay the same. But the tools and the speed you must work at are totally different.
The shared responsibility model explained
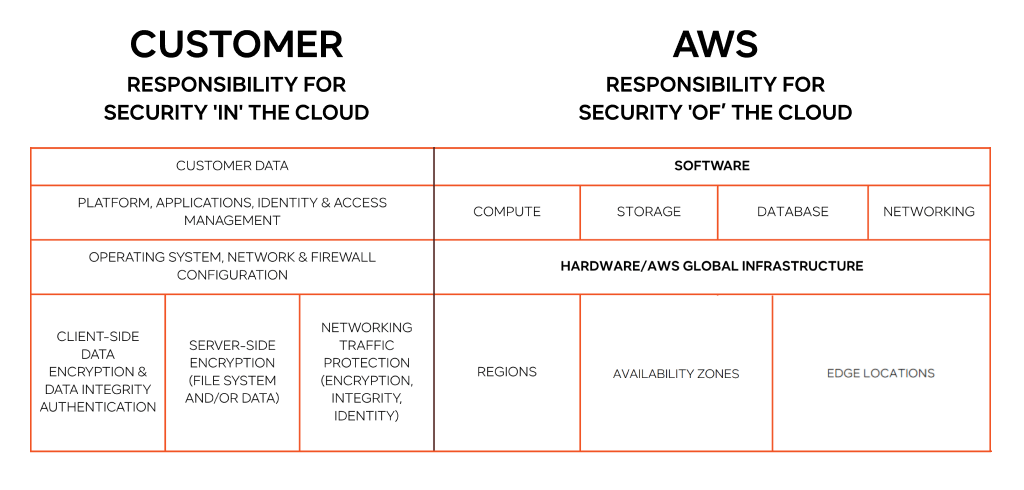
To succeed with Amazon Web Services security, you must fully understand one basic idea: the Shared Responsibility Model. This model clearly shows where AWS’s job stops and your job starts. Getting this wrong is the number one cause of cloud breaches.
AWS divides the job like this:
- AWS is responsible for “security of the cloud.”
This means AWS protects the global infrastructure. This includes the hardware, software, networks, and physical buildings that run all AWS services. It covers the virtualization software and the physical security of the data centers.
- The customer is responsible for “security in the cloud.”
This is everything you build or set up within AWS. It includes your data, operating systems, applications, network management, and all the settings for the security for AWS tools you choose to use.
This division changes depending on the type of service you choose:
| Service Type | AWS Job (Security of the Cloud) | Customer Job (Security in the Cloud) |
| IaaS (EC2, VPC) | Physical security, global networks, virtualization. | OS patching, application security, firewall setup (Security Groups), IAM management, data encryption. |
| PaaS (RDS, EKS) | OS and database patching, core infrastructure. | Database setup, network access, data encryption, IAM management. |
| SaaS (S3, DynamoDB) | Everything up to the service’s access point. | Data management (including encryption options), IAM management, policies on storage buckets, data classification. |
Quick Example: When you launch a virtual server (an EC2 instance), the responsibility is clear.
AWS secures the hypervisor (the virtualization software) and the host server.
You (the customer):
- You manage the operating system you install. If a patch is released for an OS flaw, you must apply it.
- You must set up the Security Group – that virtual firewall – to make sure only necessary traffic can get through.
- You must use IAM policies so only authorized users can access the server.
- You must encrypt the data on the attached storage (EBS volumes).
Mistakes you make in settings – like leaving an S3 storage bucket open to the public or having a weak database port – are the biggest reason for cloud security AWS breaches. Some experts say these errors cause as much as 70% of all security challenges in the cloud environment.
Why strong AWS cloud security matters
The consequences of having poor security in AWS are huge. It’s not just a tech problem. It’s a core business risk that hurts your money and your good name.
What happens when security fails?
- Data breaches and financial penalties:
A security failure can expose private customer or financial data. Studies show the global average cost of a data breach is about $4.44 million. This figure goes much higher in regulated industries. - Compliance failures:
For many fields, cloud security is required by law. Failures can lead to very large fines.- Healthcare (HIPAA): You must protect patient health information (PHI).
- Finance (PCI DSS): You must secure credit card data.
- Global Business (GDPR, CCPA): You must protect customer personal information (PII).
- Reputational damage:
A public breach destroys customer trust. It can permanently harm your brand. Fixing that reputation often costs far more than investing proactively in AWS security best practices. - Operational downtime:
Attacks like ransomware can completely shut down your critical systems. This costs you massive amounts of lost revenue and productivity.
Good security helps you grow
On the positive side, strong AWS cloud security is a business booster. It creates customer trust, which is a powerful edge over competitors. When your organization can clearly show a secure and compliant environment, you can:
- Scale without worry: Quickly launch new services and features. You know that security was built-in from the start.
- Enter new markets: Meeting global rules (like GDPR) is your ticket to doing business worldwide.
- Adopt innovation faster: Safely use new services like AI while keeping your management secure.
If you want to move quickly, you must be secure first. This proactive approach to cybersecurity is what separates the best companies from the rest.
AWS cloud security challenges
Even smart technical leaders face big problems when setting up strong AWS cloud security. The quickly changing nature of the cloud itself is often the main cause of trouble.
The five biggest problems
- Misconfigurations and human error:
This is a constant issue. It’s easy to launch infrastructure. This means it’s just as easy to launch it wrongly. A single mistake in a firewall rule, a too-broad IAM policy, or a publicly open storage bucket is an easy target for attackers. Human error is still the top risk.
- Complex Identity and Access Management (IAM):
When you have thousands of users, roles, and services in a large environment, managing permissions gets extremely difficult. Making sure everyone follows the Principle of Least Privilege – giving users only the minimum access needed – is a huge, ongoing management task.
- Securing APIs and third-party integrations:
Modern cloud applications rely heavily on APIs to connect systems. These connection points are often attacked. Also, bringing in third-party software and providers adds more complexity. You have to trust their security as well.
- Lack of visibility and control:
In a huge, multi-account environment, it’s hard to know exactly who is doing what, where, and when. This problem is worse if you use multiple clouds or a hybrid setup. It makes consistent monitoring a nightmare.
- Protecting against evolving threats:
The rise of tricky attacks, like supply chain hacks and fast-moving vulnerability exploits, demands constant attention. Your security systems must be able to detect and respond to new threats instantly.
Solving these problems takes the right technology, clear rules, and a change in culture. Every team – from developers to management – must feel responsible for security.
Here’s an important point: You don’t have to fix all this alone. Moving big workloads to AWS or fixing a complicated cloud security AWS environment needs specialized experts. These pros can make sure security is built into the foundation, not just added later. For organizations that lack in-house cloud security expertise or those who want to move fast, hiring experts is the quickest and most reliable option.
_______________________________________________________________________
Is AWS cloud security taking up all your team’s time?
Contact IT-Magic for a consultation. We’ll review your current AWS security and build a custom solution that meets your business goals. Let us help you create a stronger AWS secure cloud environment today!
_______________________________________________________________________
Essential AWS cloud security best practices
We’ve covered the problems. Now, let’s go through the clear steps and solutions that form the backbone of a strong AWS cloud security plan. These steps start with defining your policy and move to deep technical controls and continuous monitoring.
Develop a clear AWS security strategy and baseline
You need a plan before you write code or launch a service. A written security strategy is the guide for your whole AWS environment.
Step-by-step breakdown:
- Define your risk level: Find your most critical assets (data, systems). Then, decide what level of risk is okay for each one. Not everything needs the same protection.
- Establish policy and compliance rules: Clearly write down your internal security policies. Also, list the external rules you must follow (like SOC 2, ISO 27001, HIPAA, etc.).
- Adopt a security framework: Use existing standards to set up your configurations fast. The CIS AWS Foundations Benchmark is an industry standard. It gives clear, prioritized security configuration advice for the main AWS services.
- Baseline security configuration: Create a “gold standard” setup for common resources. This includes standard server images, default firewall rules, and IAM policies. All your developers must use these. This stops insecure setups from happening by chance.
Enforce Identity and Access Management (IAM) best practices
IAM management is the core of security in AWS cloud. It’s the gatekeeper for all your resources.
- Principle of least privilege:
This is mandatory. Every user, application, or service should only have the minimum permissions needed for its exact job. Don’t use the full * permission. If a service only needs to read from S3, only give it s3:GetObject on a specific bucket.
- Use IAM roles, not long-term access keys:
Give IAM Roles to your EC2 servers and other AWS services that need to talk to other AWS resources. Roles give temporary credentials that rotate automatically. This greatly reduces the risk if a long-lived access key is leaked.
- Enable MFA for everyone:
Multi-Factor Authentication (MFA) must be required for all human users. This is especially true for anyone with high-level access to your root accounts and management roles. This simple step helps stop most breaches caused by stolen login details.
- Regularly review permissions:
Use AWS tools like IAM Access Analyzer to constantly review and clean up your policies. Old user accounts or permissions that are too wide must be removed.
Encrypt data at rest and in transit
Encryption means that even if an attacker gets your data, they still can’t read it. It’s a cornerstone of security in AWS.
Data at rest: All sensitive data in services like Amazon S3, Amazon RDS, and DynamoDB must be encrypted.
- Use AWS Key Management Service (KMS) to centrally manage and rotate your encryption keys. KMS is a fully managed option that works with almost every AWS service.
- Turn on S3 Server-Side Encryption (SSE) by default for all buckets.
- Make sure RDS encryption is active when launching any new database.
Data in transit: All communication between users and your environment, and between your services, must use TLS/SSL.
- Use AWS Certificate Manager (ACM) to get and manage free SSL/TLS certificates for your Load Balancers and CloudFront.
Secure APIs and endpoints
APIs are how software systems communicate. Securing them is critical for protecting your data.
Utilize API Gateway security features. When using AWS API Gateway for your microservices, use these built-in controls:
- Authorization: Use IAM, Cognito, or custom authorizers. Make sure every request is authenticated and approved.
- Throttling: Set limits on the request rate. This prevents abuse or DDoS attacks against your systems.
- AWS WAF (Web Application Firewall): Connect WAF to API Gateway to block common web attacks like SQL injection.
Monitor and harden EC2 instances
EC2 servers are Infrastructure-as-a-Service (IaaS). This means you have the most security responsibility for them.
- Patch management: Use AWS Systems Manager Patch Manager to set up automatic patching. This ensures the operating system and all installed software are regularly updated. This is how you fix known flaws.
- Network filtering:
- Use Security Groups (SGs) as stateful firewalls for your servers. Only allow the necessary inbound traffic.
- Crucial rule: Never allow SSH (port 22) or RDP (port 3389) access from 0.0.0.0/0 (the whole internet). Limit access to a known IP range or a jump server.
- Intrusion detection/prevention (IDS/IPS): Deploy host-based intrusion detection systems. Or, use AWS Inspector. This tool runs automatic scans for vulnerabilities on your EC2 servers.
Use VPC for network isolation and protection
Your Virtual Private Cloud is your own private, isolated network in AWS. Setting it up correctly is vital for network security.
- Segmentation: Split your VPC into several subnets.
- Private subnets: Put your database servers, application logic, and other critical back-end systems here. They should not be reached directly from the internet.
- Public subnets: Only put resources that need public access here, like load balancers.
- Egress control: Use NAT Gateways to control and monitor the traffic leaving private subnets. This ensures your servers only talk to approved external networks or AWS services.
VPC Flow Logs: Turn on VPC Flow Logs. This captures detailed information about all IP traffic in your network. This data is critical for monitoring and finding suspicious network patterns later on.
Regularly back up data and enable recovery options
Security is about staying resilient. It’s not just about stopping attacks. If an incident happens, your ability to recover quickly is what matters most.
- Automate backups: Use AWS Backup to create centralized, rule-driven backup and retention management. This works for many different services (EBS, RDS, DynamoDB, etc.).
- Disaster Recovery (DR) planning: Have a clear plan for Disaster Recovery (DR). Use cross-region replication for your most critical data. If your main region fails, your data can be restored somewhere else.
- Test recovery: You must regularly test your recovery process. A backup that you never test is a risk.
Collect and protect logs with CloudTrail and CloudWatch
Logs are the single source of truth for all activity in your AWS environment. Without them, you can’t detect a breach or figure out how it happened.
- AWS CloudTrail: You must turn on CloudTrail. It records every action and API call across your AWS accounts. Ensure CloudTrail is on globally. Store the logs in an encrypted S3 bucket. Limit access to these logs very strictly (even for high-level accounts).
- Amazon CloudWatch: Use CloudWatch for real-time monitoring of performance and system logs. Set up alarms for security events. This includes changes to IAM policies or unusual API calls.
- Centralization and SIEM: Gather all your security logs (CloudTrail, VPC Flow Logs, etc.) into one dedicated security accounts S3 bucket. Send this data to a Security Information and Event Management (SIEM) solution (like Splunk). This allows for deep threat analysis.
Automate security operations (SOAR, CSPM, IaC)
Given the huge scale and speed of AWS, manually checking security and fixing issues isn’t possible. Automation is the only way to achieve consistent AWS cloud security.
- Security as Code (IaC): Use tools like AWS CloudFormation or HashiCorp Terraform. Write your infrastructure and its security controls in code. By using code, you can test it, save versions, and apply security best practices the same way across all your environments.
- Cloud Security Posture Management (CSPM): Use a CSPM solution (AWS Config or another tool). This constantly checks your AWS setups against your compliance rules (like the CIS Benchmark). If a developer accidentally makes a storage bucket public, the CSPM tool flags it instantly.
- Security Orchestration, Automation, and Response (SOAR): Set up SOAR using AWS Lambda functions. If GuardDuty detects a compromised credential, a Lambda function can automatically shut down that credential and isolate the affected server in seconds.
Implement real-time threat detection and response
Being proactive means your detection cuts the time attackers can spend inside your environment. This greatly reduces the cost of a breach.
- Amazon GuardDuty: This is a critical security solution. GuardDuty uses machine learning to constantly check your AWS accounts for bad activity. It can detect things like unauthorized bitcoin mining or compromised servers talking to bad IP networks.
- AWS Security Hub: Use Security Hub to bring all your security alerts together. It takes alerts from GuardDuty, Inspector, WAF, and other providers and tools. This gives your cybersecurity team one easy view to prioritize alerts.
- AWS Detective: Use AWS Detective to make investigations simpler. Detective analyzes logs and uses machine learning to map out how all your resources interact. Investigators can quickly find the root cause of an incident.
Conduct regular audits and security reviews
Even with automation, you need to check that everything is working. Regular audits confirm that your controls are strong and that your organization meets all its compliance rules.
- Internal audits: Do continuous self-checks using AWS Config rules against your baseline.
- Third-party audits: Hire outside auditors to confirm your compliance with standards like SOC 2, ISO 27001, and PCI DSS. This is often required for big business deals.
- Penetration testing (pen-testing): Run controlled attacks against your applications and networks. This finds flaws before a real attacker does. Be sure to follow AWS rules for getting permission to run these tests.
- Continuous improvement: Don’t treat audit findings as failures. Treat them as chances to get better. Use the results to update your security-as-code templates, fix IAM policies, and improve your incident response plans.
What’s next? Building this level of AWS cloud security takes a lot of time and specialized expertise. If your developers are focused on products and your IT management team is overwhelmed, achieving this deep defense can seem out of reach.
AWS cloud security tools and features
A major benefit of using AWS is how well its native security services work together. These tools were designed to integrate easily. This gives you a strong, layered defense solution.
AWS native security services
- AWS Identity and Access Management (IAM): The core service for controlling access. It lets you create users and roles. It uses policies to define permissions. It’s the most critical control in your management toolkit.
- Amazon GuardDuty: A real-time threat detection service. It checks your AWS accounts for bad activity non-stop. It helps you detect compromises immediately.
- Amazon Inspector: An automated vulnerability management service. It keeps scanning your AWS workloads (like servers and container images) for software flaws and accidental network exposure.
- AWS WAF (Web Application Firewall): Protects your web applications or APIs from common web attacks that could crash your systems or steal data. You can put it in front of CloudFront, API Gateway, and Load Balancers.
- AWS Key Management Service (KMS): A managed service. It makes it easy to create and control the encryption keys you use. This ensures key management is central and audited.
Logging and monitoring solutions
- AWS CloudTrail: Provides a record of every management action taken across your AWS infrastructure. It’s used for auditing and compliance checks.
- Amazon CloudWatch: Gathers monitoring data, logs, and events. It gives you one place to see how your operations are running. It also lets you set up alarms and automated responses.
- AWS Config: Continuously monitors and records how your AWS resources are set up. It lets you automatically check these settings against your required baselines.
Integration with third-party security tools
While AWS native tools are powerful, many organizations need to connect them with third-party providers. This is often for hybrid or multi-cloud management or specialized needs.
- SIEM Integration: Popular Security Information and Event Management (SIEM) systems like Splunk and Datadog can take in logs and alerts from CloudTrail, GuardDuty, and Security Hub. This gives you one clear view of security across your cloud and on-premise systems.
- Network security appliances: Virtual appliances from providers like Palo Alto can be deployed inside your VPC. They give you advanced firewall management and specialized threat detection.
- Hybrid visibility: Third-party solutions are often necessary for seeing everything and setting policies consistently in hybrid environments. This is where you connect your existing on-premise networks and identity systems with your new cloud infrastructure.
Proactive cloud security approaches
The best and most modern AWS cloud security plans are proactive. They focus on stopping threats before they become a problem, rather than just reacting to them.
Continuous monitoring and automated remediation
This approach ensures your security setup is always correct.
- Detect and fix: Continuous monitoring uses tools like AWS Config and GuardDuty to detect when a setting changes or a suspicious event happens.
- Automated remediation: Once an issue is detected, an automated workflow (like a Lambda function) instantly fixes the problem. For example, if AWS Config detects that encryption was turned off on a storage bucket, the Lambda function automatically turns it back on. This closes the exposure window right away.
Security as code and DevSecOps integration
The “Shift-Left” idea means building security into the development process from the very start.
- Integrate security in CI/CD: Developers must use automated software scanning tools inside their deployment pipelines. This ensures that insecure code or infrastructure code is detected before it gets deployed live.
- Standardized templates: Developers should use only pre-approved, secure templates (Security as Code). These templates have the necessary controls built in by default, like encryption and least-privilege IAM roles.
Unifying on-prem and cloud security policies
For most large organizations, the AWS environment is an extension of their existing infrastructure. Security management must be the same across this hybrid space.
- Standardize policies: Work toward one set of security practices that applies everywhere – in the cloud and on-prem. A user’s login requirements should be the same for all applications.
- Identity Federation (SSO): Use identity solutions (like Active Directory) to manage all user accounts. Use Single Sign-On (SSO) to give access to AWS. This centralizes user management and enforces MFA consistently.
- AWS Control Tower: For large organizations with many AWS accounts, Control Tower helps automate setting up a secure, multi-account environment. It applies guardrails and best practices across the whole organization.
How to respond to security incidents in AWS
A great defense plan assumes a breach will happen. So, having a tested Incident Response (IR) plan is critical. The goal is to stop and remove the threat as fast as you can.
The incident response plan outline
A good plan follows a clear lifecycle:
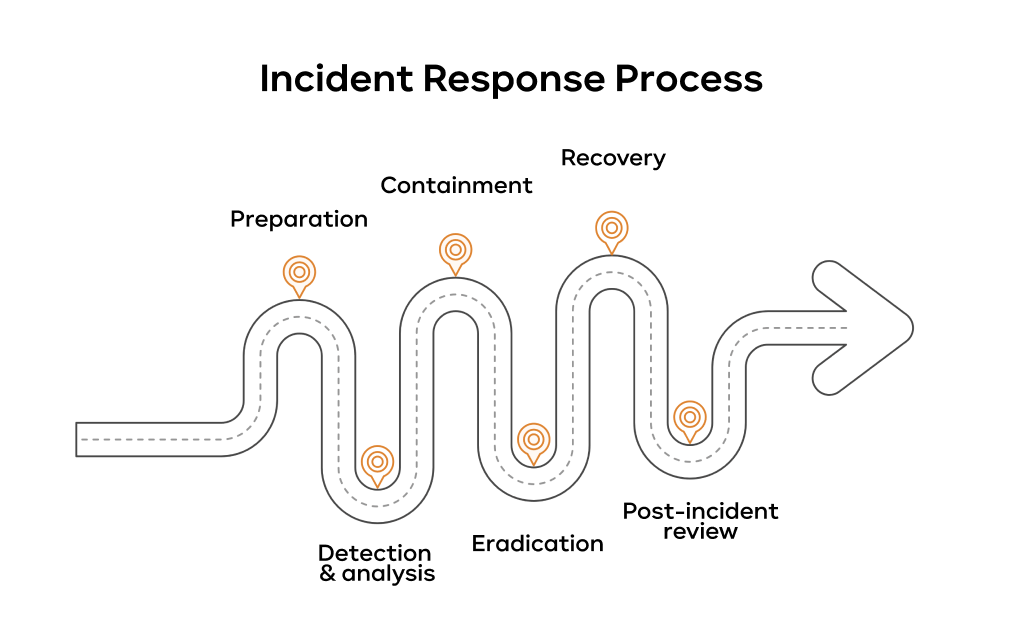
- Preparation: This is the planning stage. It includes:
- Creating and testing your IR playbooks.
- Defining communication rules (who calls whom, inside and outside the company).
- Making sure logging (CloudTrail, VPC Flow Logs) is on and secured.
- Creating “break glass” accounts for emergency use, with strong MFA.
- Detection & analysis: The moment you find a threat.
- Tools like GuardDuty, Security Hub, and CloudWatch alarms flag the bad activity.
- Your team uses AWS Detective and centralized logs to figure out the scope, the method, and the source of the attack.
- Containment: The most urgent part. Stop the damage!
- Immediately isolate compromised servers by changing their Security Groups.
- Revoke any stolen IAM login details.
- Block bad IP addresses using AWS WAF or NACLs.
- Eradication: Removing the root cause and any hidden threats.
- Patching the security flaw that was used.
- Deleting any backdoor accounts left by the attacker.
- Restoring systems from a trusted backup.
- Recovery: Bringing systems back online safely.
- Setting up new monitoring to ensure the threat is gone.
- Restoring operations to meet your recovery time goals.
- Post-incident review: A review (with no blame) to figure out how it happened and how your response can be better next time. This information helps improve your best practices and automation.
Practice and preparation
- Define playbooks: Write clear guides for common scenarios: “S3 Bucket Exposed,” “Stolen IAM Credential,” and “DDoS Attack.”
- Simulate and test: You must regularly run security drills. Test your team’s readiness and check if your playbooks work under pressure. A real incident is the worst time to find out your plan has flaws.
Conclusion: Building a secure AWS environment
Building a secure AWS environment is a commitment. It’s a journey, not a destination. We’ve seen that true AWS cloud security relies on two simple ideas: understanding the Shared Responsibility Model and always applying the essential AWS security best practices.
You can minimize your risk by: carefully using the Principle of Least Privilege through IAM management, encrypting all your data with KMS, using GuardDuty for fast threat detection, and automating your security processes. This strong, layered defense lets your organization grow with confidence in the cloud environment.
The shift from old IT security to cloud security is major. It trades physical defenses for software-defined controls based on identity. It’s a challenging but valuable effort. It leads to a more resilient, compliant, and cost-effective infrastructure.
Need help to set up and manage a large, complex AWS secure cloud infrastructure?
We can provide a long-term security solution that strengthens your defense and gives you peace of mind. Let us manage your AWS cloud security so you can focus on your strategic management goals.
FAQ
What are the most important AWS security best practices?
Strong AWS cloud security rests on a few simple foundations. The most important is Identity and Access Management (IAM). You must stick to the Principle of Least Privilege. Never give more permissions than needed. Second, encrypt data at rest and in transit using AWS KMS. Third, always have monitoring and threat detection turned on using AWS CloudTrail and GuardDuty. Last, automate your security processes (Security as Code) for consistency and quick fixes. This layered strategy is the best defense.
What is the best way to secure the root user in AWS?
The root user account has total control over your entire AWS environment. You can’t take away its power. So, AWS security best practices say you must do this: 1) Turn on Multi-Factor Authentication (MFA) right away. 2) Never use the root user for daily work (not even for admin tasks). Create a standard admin IAM user for that. 3) Store the root user’s login details securely (in a safe, encrypted place) and only use the account for the few things only the root user can do.
How does AWS ensure compliance with security standards?
AWS ensures compliance through the Shared Responsibility Model. AWS is responsible for the security of the cloud. Their global infrastructure is constantly audited. It holds certifications like SOC 2, ISO 27001, and PCI DSS eligibility. AWS provides these reports to customers. However, compliance in the cloud is your job. Your organization must set up its applications, data, and access controls correctly (like encrypting data and using IAM) to meet the final compliance rules for your industry.
Can automation fully replace manual cloud security processes?
No, automation can’t fully replace human security work. But it should handle most of the repetitive, high-volume tasks. Automation (using SOAR and Security as Code) is excellent at enforcing configurations, monitoring logs, finding threats in real-time, and doing simple, fast fixes. Human oversight is still critical. Humans are needed for: defining policies, doing complex threat hunting, designing automated workflows, and the overall strategic management of the security program. The goal is to use automation to turn your cybersecurity team into strategic thinkers, not manual laborers.